azure

Prepárese para el futuro con Azure cloud

Confíe en su nube
azure cloud servicios en la nube de microsoft
Obtenga seguridad desde el principio—con el respaldo de un equipo de expertos y un cumplimiento normativo proactivo en el que confían empresas, administraciones públicas y startups.
investigación y desarrollo de la seguridad
Aproveche la seguridad multicapa que se proporciona en los centros de datos, la infraestructura y las operaciones, con expertos en ciberseguridad que los supervisan activamente para proteger los recursos y los datos de su empresa.

Un firme compromiso con la privacidad
Usted controla sus datos, en los que se basan sus experiencias. Nuestro principio básico de privacidad es que usted es el propietario de sus datos. Nunca los usaremos con fines publicitarios o de marketing.
6,5 billones de señales de amenazas analizadas a diario
Haga que la detección y la respuesta a amenazas sea más inteligente y rápida con señales de seguridad basadas en inteligencia artificial que modernizan las operaciones de seguridad.
Prepárese para el futuro
La innovación continua de Microsoft—sustenta el trabajo de desarrollo que realiza hoy y sus ideas de productos futuros.

Más de 1000 características nuevas en Microsoft Azure Cloud en el último año
Cree soluciones con los últimos avances en inteligencia artificial, cadena de bloques, Kubernetes, contenedores y bases de datos para estar siempre a la vanguardia.
La cartera de inteligencia artificial más completa
Transforme su negocio y sus aplicaciones con un conjunto completo de servicios cognitivos. Incorpore a sus aplicaciones, sitios web y bots algoritmos inteligentes que permiten ver, oír, hablar, comprender e interpretar las necesidades de los usuarios con formas de comunicación naturales.
Análisis 14 veces más rápidos que cuestan un 94 % menos
Convierta los datos en conclusiones con un nivel extraordinario de rendimiento, seguridad y velocidad. Nuestra solución de análisis de nivel empresarial supera a la competencia, cuesta menos y es totalmente compatible con las herramientas de desarrollo, inteligencia empresarial y ciencia de datos que ya tiene.

Trabaje en un entorno híbrido sin problemas
En el entorno local, en la nube y en el perímetro—Nos adaptamos a usted. Integre y administre sus entornos con herramientas y servicios diseñados para la nube híbrida.
Plataforma de identidad unificada
Mejore la seguridad, simplifique el acceso y establezca directivas inteligentes en diversos entornos con una sola plataforma de identidad en la que confía el 90 % de las empresas de todo el mundo.
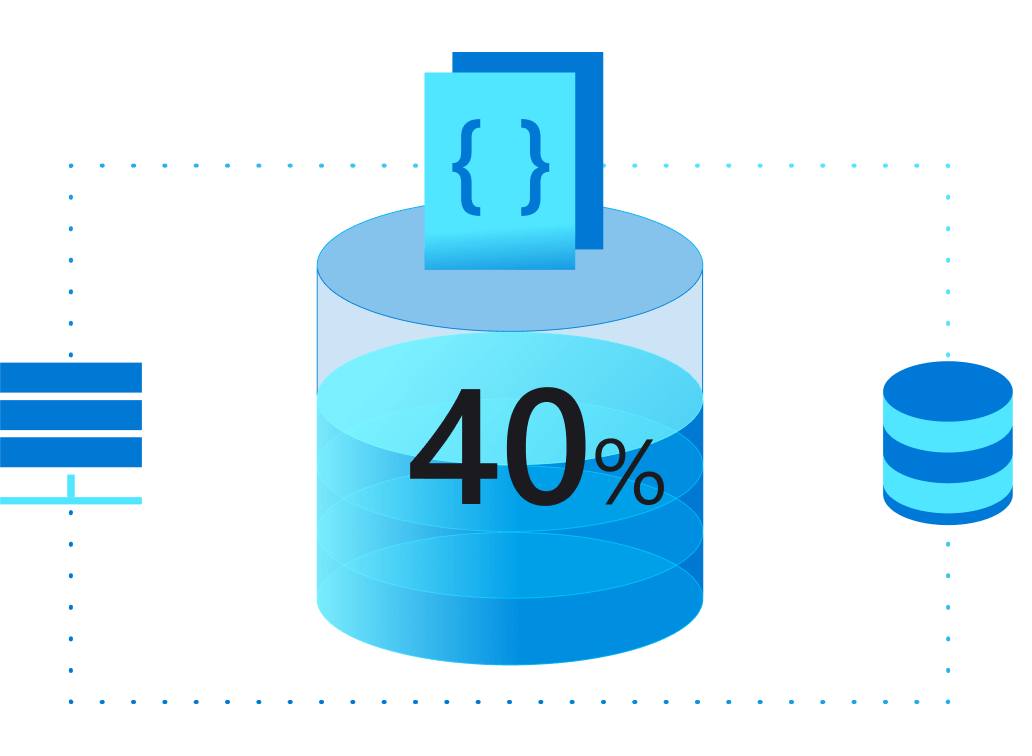
Windows Server y SQL Server por menos
Aproveche la Ventaja híbrida de Microsoft Azure cloud y ahorre un 40 % en máquinas virtuales con su inversión actual en licencias de SQL Server o Windows Server.

Inteligencia artificial en el perímetro
Implemente Azure Cognitive Services en contenedores para analizar la información cerca del mundo físico donde se encuentran los datos. Ofrezca conclusiones en tiempo real y experiencias inmersivas con una elevada capacidad de respuesta y sensibles al contexto.
Productos Microsoft Azure cloud

Azure Active Directory
Sincronice los directorios locales y habilite el inicio de sesión único.

Azure DevOps
Servicios para que los equipos compartan código, supervisen el trabajo y distribuyan software.

Azure Stack
Dé rienda suelta a la innovación con aplicaciones de nube híbrida.

Data Box
Dispositivos y soluciones para la transferencia de datos a Azure y el proceso perimetral.

Security Center
Unifique la administración de seguridad y habilite la protección contra amenazas avanzada para cargas de trabajo en la nube híbrida.

SQL Database
Motor de datos de superficie pequeña y optimizado para el perímetro con inteligencia artificial integrada.

Azure cloud Security Center
Obtenga una funcionalidad inigualable de administración de la seguridad híbrida y de protección contra amenazas
Active la protección que necesita
Microsoft utiliza una gran variedad de controles físicos, de infraestructura y operativos para proteger Microsoft Azure Cloud, pero estas son medidas adicionales que usted debe llevar a cabo para ayudar a proteger sus cargas de trabajo. en conclución Utilice Security Center para fortalecer con rapidez sus medidas de seguridad y proteger sus recursos frente a amenazas.
Administración de las medidas de seguridad para sus cargas de trabajo en la nube
Evalúe sus medidas de seguridad con rapidez mediante Puntuación de seguridad. Es decir esta característica proporciona recomendaciones con valores numéricos para ayudarle a clasificar las respuestas por orden de prioridad.
Por lo tanto asegúrese de utilizar los procedimientos recomendados y de corregir los errores de configuración habituales en los recursos de infraestructura como servicio (IaaS) y de plataforma como servicio (PaaS) de Azure, que pueden ser, por ejemplo:
- No implementar las actualizaciones del sistema en las máquinas virtuales (VM).
- Exposición innecesaria a Internet a través de puntos de conexión que están de cara al público.
- Datos no cifrados en tránsito o en almacenamiento.
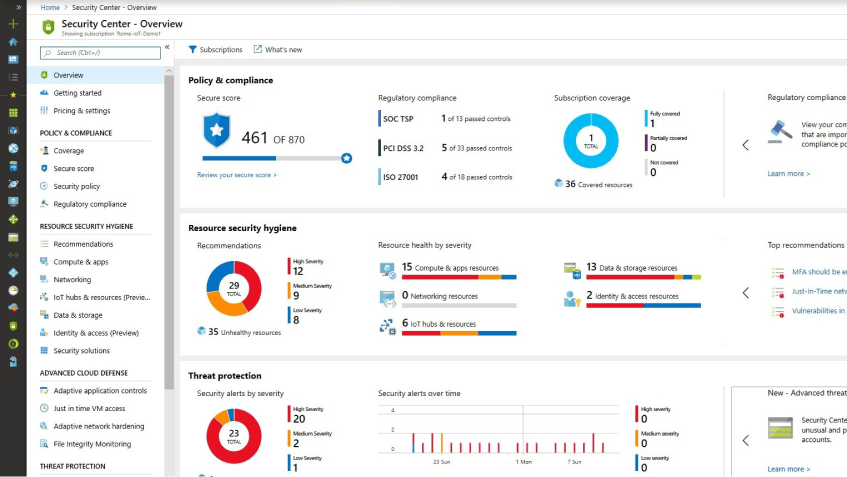
Una vez que los haya solucionado, implemente fácilmente soluciones de Microsoft y de asociados directamente desde Azure Portal.
Personalice su directiva de seguridad para centrarla en lo necesario (por ejemplo, compruebe si hay firewalls de aplicaciones web o cifrado en el almacenamiento) y aplique la directiva a varias suscripciones de Azure. Consiga visibilidad de su entorno para comprobar el cumplimiento con normas como CIS, PCI DSS, SOC e ISO.
Proteja sus servidores Linux y Windows
Security Center ayuda a proteger los servidores y clientes de Windows con Protección contra amenazas avanzada de Microsoft Defender. Además, protege los servidores Linux con análisis del comportamiento. Por cada ataque que se intenta o se lleva a cabo, usted recibe un informe detallado y soluciones recomendadas.
Ademas proteja los servidores que se ejecutan en Azure y otras nubes con controles avanzados. El acceso Just-in-Time a máquinas virtuales reduce el área expuesta a ataques por fuerza bruta mediante RDP/SSH, una de las amenazas más comunes, con más de 100 000 intentos de ataque en Azure Virtual Machines al mes. Utilice el nivel Estándar para mitigar esta amenaza.
Ciertamente a medida que agrega aplicaciones a máquinas virtuales en Azure, bloquee aplicaciones malintencionadas, incluidas las que no mitigan las soluciones antimalware, usando controles de aplicaciones adaptables. Machine Learning aplica automáticamente nuevas directivas de lista blanca de aplicaciones a las máquinas virtuales.
Proteja sus aplicaciones nativas de la nube
Solucione vulnerabilidades de las aplicaciones web, como complementos y páginas web expuestos, que son un objetivo frecuente de los atacantes. El nivel Estándar ayuda a proteger las aplicaciones que se ejecutan en Azure App Service, porque marca el comportamiento que podría pasar a través de los instrumentos de firewall de aplicaciones web. También ayuda a proteger otros servicios en la nube, como VM Scale Sets y Containers.
Proteja sus datos
Los avances en el campo de los macrodatos y el aprendizaje automático hacen posible que Security Center pueda detectar patrones de consulta y accesos anómalos en las bases de datos, ataques por inyección de código SQL y otras amenazas cuyo objetivo sea sus bases de datos de Azure SQL Database. Reciba alertas de actividad sospechosa y acciones recomendadas para investigar y mitigar estas amenazas. Detecte, clasifique, etiquete y proteja los datos confidenciales de sus bases de datos. Detenga las amenazas en su instancia de Azure Storage, incluidos el acceso desde una ubicación inusual, el acceso anónimo inusual, la extracción de datos inusual o una eliminación imprevista.
Proteja su solución de IoT
Obtenga una vista unificada de la seguridad de todas sus cargas de trabajo locales y en la nube, incluida su solución de Azure IoT. Detecte e incorpore automáticamente nuevos dispositivos y aplique directivas de seguridad a sus cargas de trabajo (dispositivos Leaf, Edge e IOT Hub) para asegurar el cumplimiento de estándares de seguridad. Supervise de forma constante la seguridad de los dispositivos IoT, las máquinas, las redes y los servicios de Azure, incluida su solución de Azure IoT, desde los dispositivos perimetrales hasta las aplicaciones, usando cientos de valoraciones de seguridad integradas, o bien cree las suyas propia en un panel central. Optimice su configuración de seguridad y mejore su puntuación de seguridad con recomendaciones que le ayudarán a tomar medidas en las máquinas virtuales, las redes, las aplicaciones y los datos.
Configure y amplíe la seguridad más allá de Microsoft Azure Cloud con rapidez
- Amplíe la administración de las medidas de seguridad y la protección contra amenazas a las máquinas virtuales del entorno local.
- Aprovisione fácilmente un agente para las cargas de trabajo de servidor que se ejecutan en el entorno local.
- Evalúe su seguridad con una vista unificada de sus cargas de trabajo de nube híbrida.
- Conecte herramientas y procesos que ya utiliza, como un sistema SIEM (Administración de eventos e información de seguridad), o integre soluciones de seguridad de asociados.
- Reduzca la inversión y reasigne los recursos usando controles de seguridad propios o de terceros.
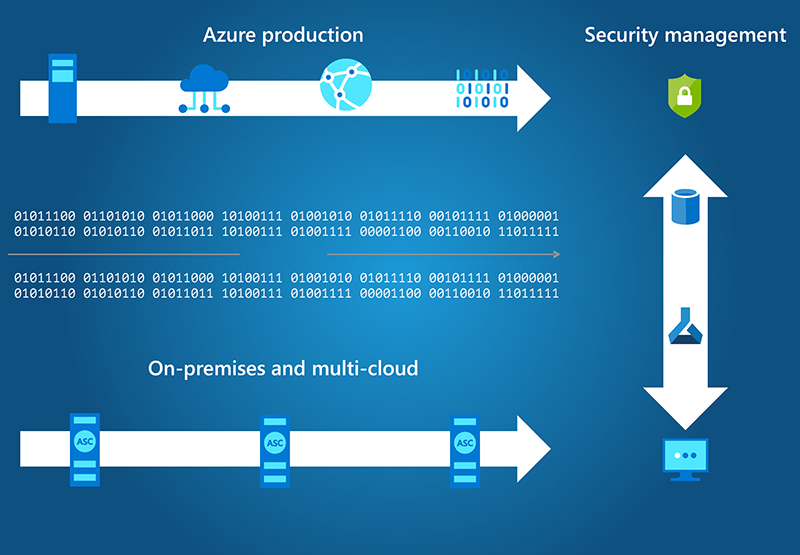
¿Cómo funciona Azure Security Center?
Cuando se activa Security Center, se implementa automáticamente un agente de supervisión en las instancias de Microsoft Azure Cloud Virtual Machines. En las máquinas virtuales locales, debe implementar el agente manualmente. Security Center comienza por evaluar el estado de seguridad de todas sus máquinas virtuales, redes, aplicaciones y datos.
Nuestros motores de análisis analizan los datos y Machine Learning los sintetiza. Security Center proporciona recomendaciones y alertas de amenazas para proteger sus cargas de trabajo. Sabrá de inmediato si ha tenido lugar un ataque o alguna actividad anómala.
Azure DevOps
Transformación de su negocio con supervisión moderna
Recopile y analice los datos de telemetría de sus entornos de Azure y locales y actúe sobre dichos datos. En definitiva Microsoft Azure Cloud Monitor lo ayuda a maximizar el rendimiento y la disponibilidad de las aplicaciones y a identificar proactivamente los problemas en segundos.

Unificado
Almacene y analice toda la telemetría operativa en un almacén de datos centralizado, totalmente administrado y escalable optimizado para el rendimiento y el costo.

Inteligente
Pruebe sus hipótesis y revele patrones ocultos utilizando el motor analítico avanzado, el lenguaje de consulta interactivo y las construcciones integradas de aprendizaje automático.

Abierto
Se integra con conocidas herramientas de DevOps, administración de problemas, administración de servicios de TI y administración de información de seguridad y eventos.
Supervisar las aplicaciones de Microsoft Azure Cloud
Obtenga todo lo que necesita para supervisar la disponibilidad, el rendimiento y el uso de las aplicaciones web, tanto si están hospedadas en Azure como en un entorno local. Asimismo Azure Monitor admite lenguajes y marcos populares, como .NET, Java y Node.js, y se integra con procesos y herramientas DevOps como Azure DevOps, Jira y PagerDuty. Realice un seguimiento de los flujos, las solicitudes y los tiempos de respuesta de métricas en vivo, y los eventos.
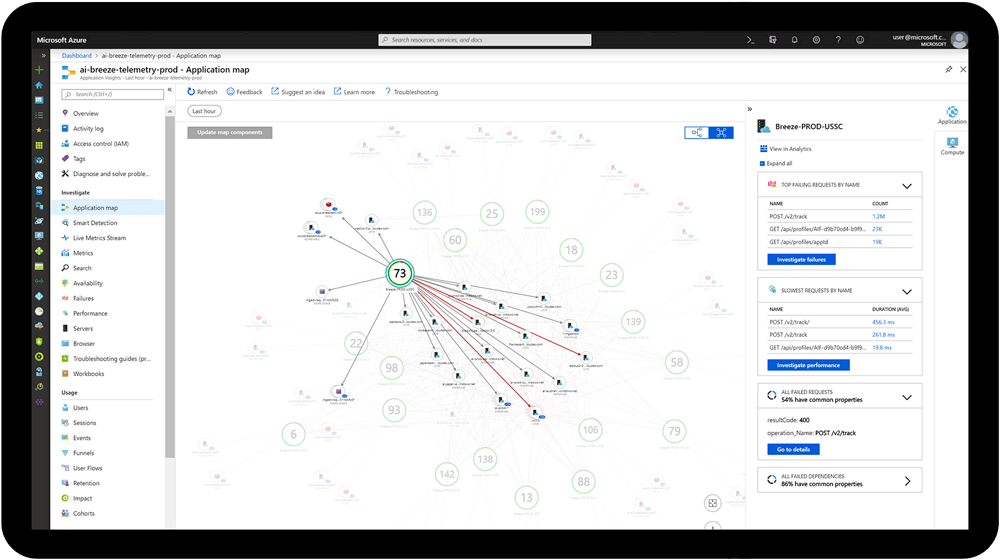
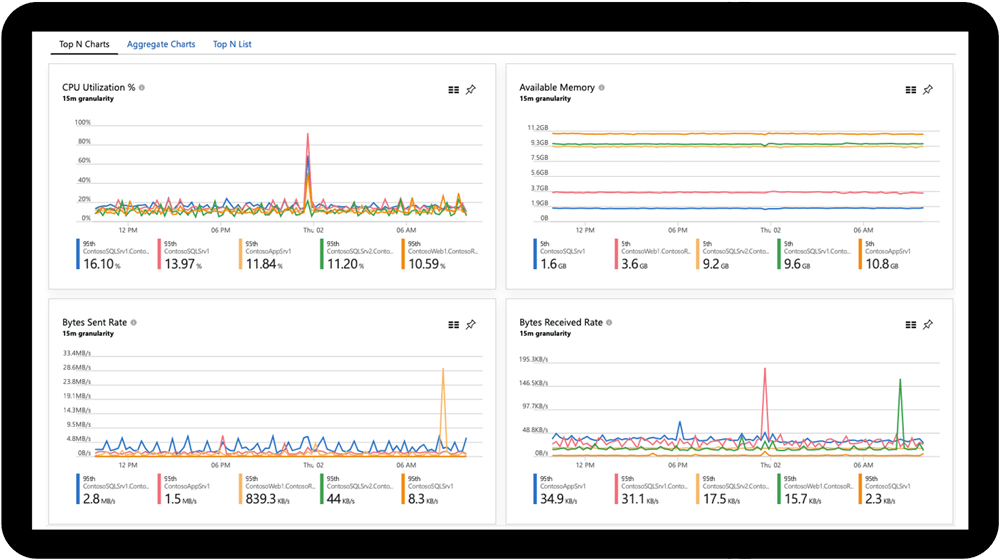
Monitorización de su infraestructura
Analice y optimice el rendimiento de su infraestructura, incluidas las máquinas virtuales (VM), Azure Kubernetes Service (AKS), Azure Storage y las bases de datos. Asimismo supervise sus máquinas virtuales Linux y Windows y su estado y dependencias, todo en un solo mapa.
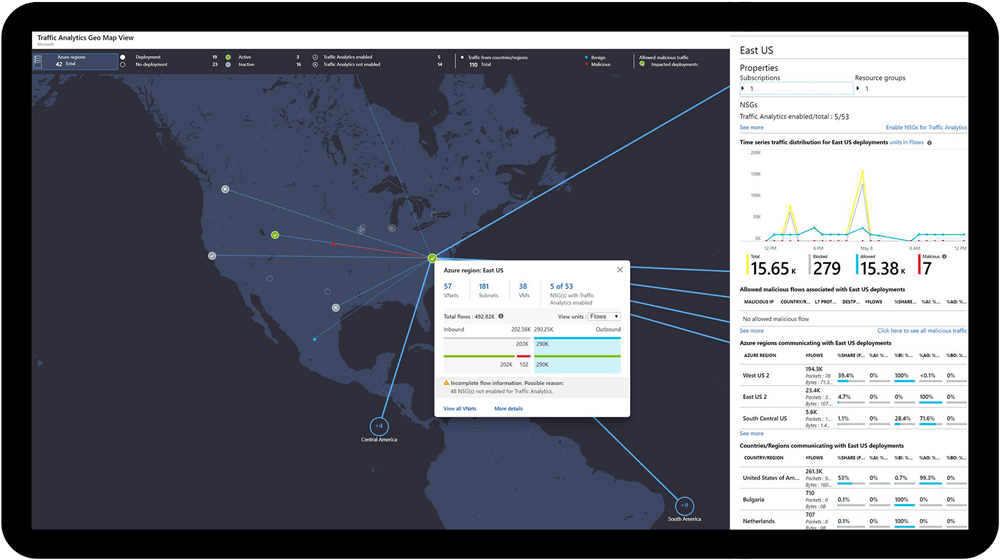
Supervisión de la red
Supervise y diagnostique problemas de red sin iniciar sesión en las máquinas virtuales. Asimismo active una captura de paquetes, diagnostique problemas de enrutamiento, analice los registros de flujo de grupos de seguridad de la red y obtenga visibilidad y control sobre la red de Azure.
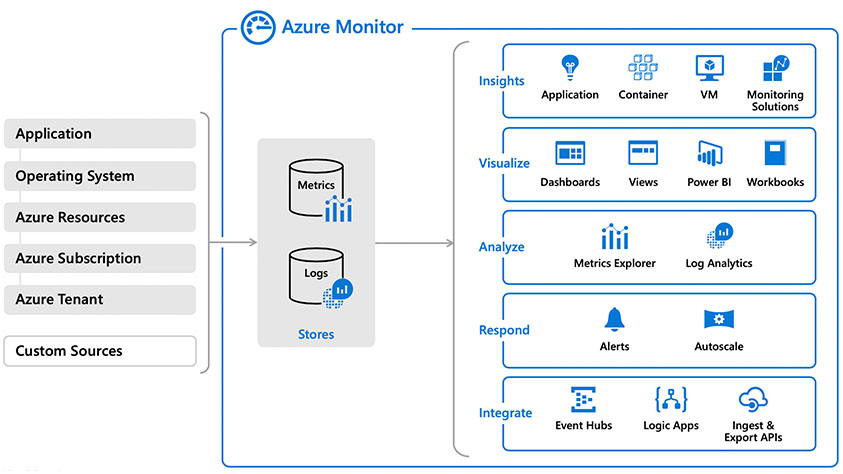
Funcionamiento de Azure Monitor
Azure Monitor recopila telemetría de supervisión de diversas fuentes de entornos locales y de Azure. Las herramientas de administración, como las de Azure Security Center y Azure Automation, además insertan datos de registro en Azure Monitor.
Asimimo el servicio agrega y almacena esta telemetría en un almacén de datos de registro que está optimizado para el costo y el rendimiento. Después de eso analice los datos, configure alertas, obtenga vistas de extremo a extremo de sus aplicaciones y use conclusiones controladas por el aprendizaje automático para identificar y resolver problemas rápidamente.

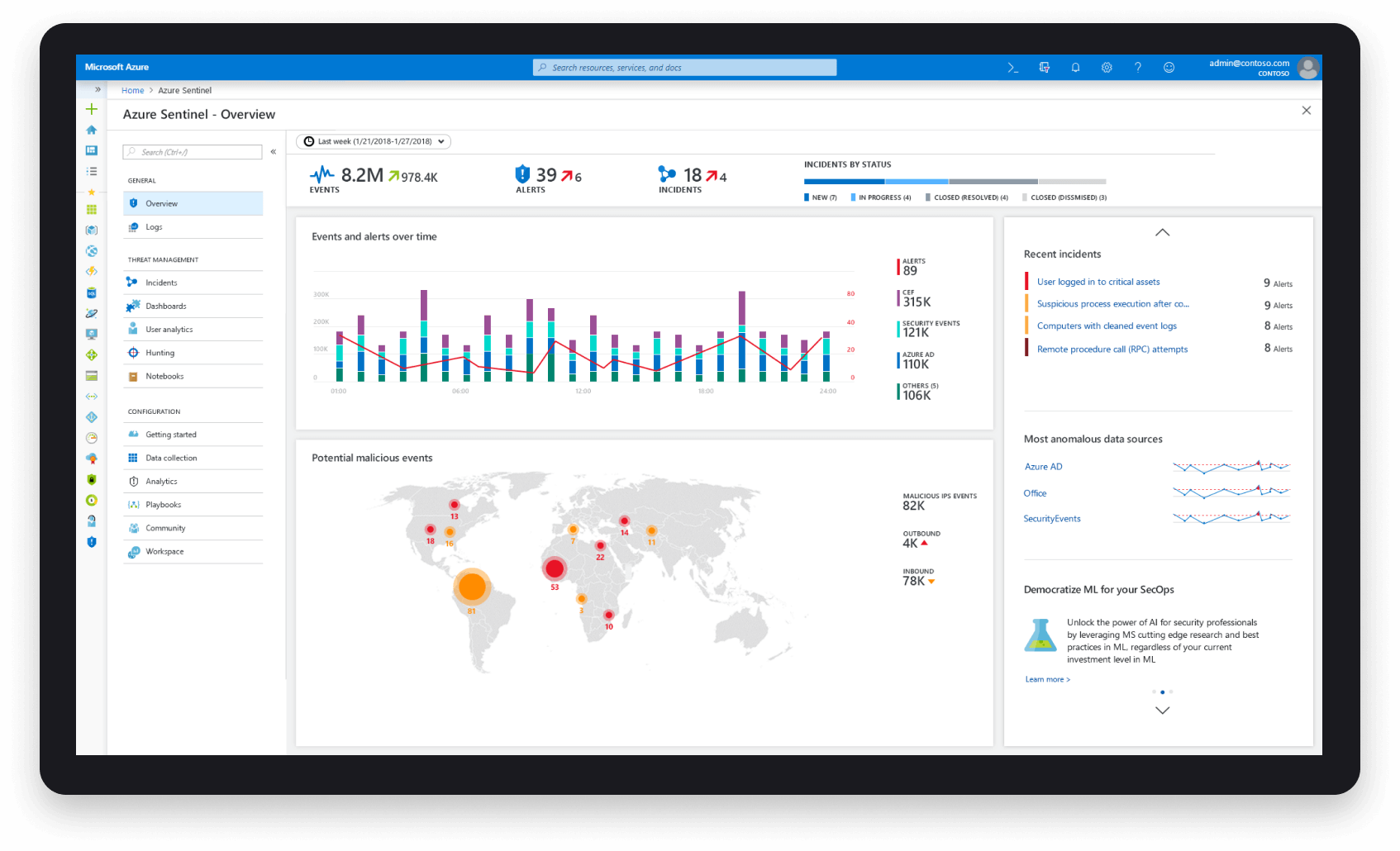
Azure Sentinel
Cree operaciones de seguridad de nueva generación con la nube e inteligencia artificial
Un vigilante a su lado. Análisis de seguridad inteligente para toda su empresa.
Vea y detenga las amenazas antes de que causen daños, con tecnología SIEM reinventada para un mundo moderno. Asimismo a.zure Sentinel le ofrece una vista completa de su empresa. además aproveche el conocimiento de la nube y a gran escala que ha adquirido Microsoft durante décadas de trabajo en materia de seguridad.
Utilice inteligencia artificial (IA) para detectar y responder a amenazas de un modo más inteligente y con más rapidez. Además elimine la configuración y el mantenimiento de la infraestructura y escale los recursos de forma elástica para satisfacer sus necesidades de seguridad, al tiempo que reduce los costos de TI.

Recopile
Datos a escala de nube de todos los usuarios, dispositivos, aplicaciones y de toda la infraestructura, tanto en el entorno local como en diversas nubes.

Detecte
Amenazas que antes no se descubrían y minimice los falsos positivos usando análisis e información de amenazas sin parangón de Microsoft.
Investigue
Las amenazas con inteligencia artificial y busque actividad sospechosa a escala, aprovechando el trabajo en ciberseguridad que ha llevado a cabo Microsoft durante décadas.
Responda
A los incidentes con rapidez usando la orquestación y la automatización de tareas comunes integradas.

Escala y velocidad de nube sin límites
Invierta en seguridad, no en la configuración y el mantenimiento de la infraestructura, con la primera solución SIEM nativa en la nube de uno de los principales proveedores de nube. En la misma línea no permita nunca más que un límite de almacenamiento o de consultas le impida proteger su empresa. Comience a usar Azure Sentinel de inmediato. Se escala automáticamente según las necesidades de su organización y solo paga por los recursos que necesita.
Inteligencia artificial en su entorno
Céntrese en encontrar amenazas reales con rapidez. Reduzca el ruido de los eventos legítimos con aprendizaje automático integrado y conocimiento basado en el análisis de billones de señales a diario. Agilice la búsqueda proactiva de amenazas con consultas integradas que son el resultado de años de experiencia en materia de seguridad. Vea una lista de alertas por orden de prioridad, obtenga análisis correlacionados de miles de eventos de seguridad en solo unos segundos y visualice el ámbito completo de cada ataque. Simplifique las operaciones de seguridad y agilice la respuesta a las amenazas con automatización y orquestación integradas de tareas y flujos de trabajo comunes.

Se adapta perfectamente a todas sus herramientas
Recopile y conéctese a datos de todos sus orígenes, como usuarios, aplicaciones, servidores y dispositivos que se ejecuten en el entorno local o en la nube. Intégrelo con sus herramientas actuales, ya sean aplicaciones empresariales, otros productos de seguridad o herramientas propias, y utilice sus propios modelos de Machine Learning. Optimícelo para sus necesidades incorporando sus propias conclusiones, detecciones personalizadas, modelos de Machine Learning e información de amenazas.
Contactenos para más información
Es decir, en otras palabras, para aclarar Pero, sin embargo, por otro lado Por ejemplo, por ejemplo Sobre todo, lo más importante, ciertamente En primer lugar / en segundo lugar, además y, además, además Mientras tanto, durante, posteriormente, después de eso Asimismo, de manera similar, en la misma línea En conclusión, en resumen, en definitiva
