AvePoint Policies & Insights

FREEDOM FOR USERS
SECURITY FOR BUSINESS

SECURE COLLABORATION MADE EASY WITH PI
Organizations need to support rapid user adoption while minimizing collaboration risk. Itco Cloud and AvePoint bring you the best solution to reduce the burden of IT. Policies & Insights for Microsoft 365 is the security tool to find, prioritize, fix, and enforce security controls across Teams, Groups, SharePoint, and OneDrive.
With PI, organizations can unleash user adoption and the power of Microsoft 365 sensitive information types and security controls, without becoming a security expert. PI guides admins towards appropriate controls with prioritized insights. Set robust controls from one place, that get enforced automatically.
Transform basic security services & reporting
Security and permissions audits and reports have never been easier. PI provides a single pane for everything you need to prove that Teams, Sites, Groups, and OneDrive are under control. Report, audit, and fix issues in bulk to save time and money.
Whether managing a client’s Microsoft 365 tenant—or just giving them tools that rule—we’ll automatically enforce security and configuration policies, create audit reports, make permissions changes, and more without limiting the work of the teams.
Keep your customers´ workspaces secure. We give you tools to help build trust and deliver results, making sure your clients come back again and again.
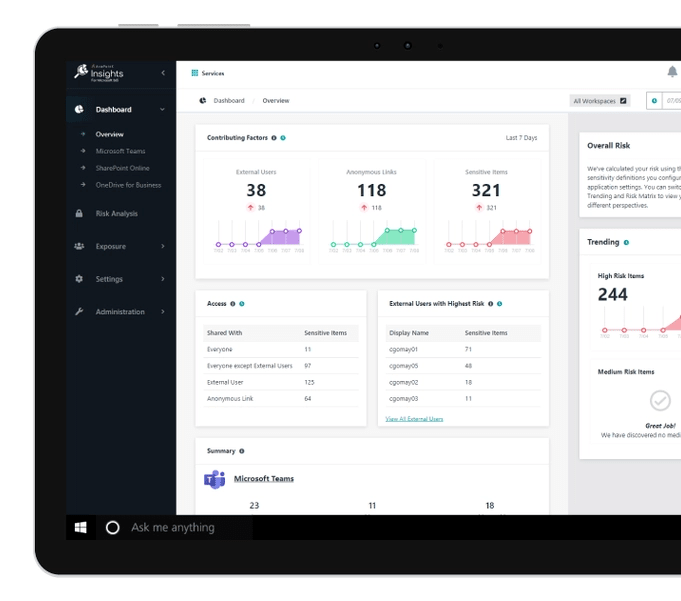

Find and Prioritize
- Aggregate access, sensitivity, and activity data
- Regulations and information types define risk
- Prioritize to easily expose issues and focus on what matters.

Monitor and Correct
- Security dashboards highlight anonymous links and exposed sensitive data
- Drill down on known and potential issues
- Fix as you go – edit permissions in batch

Apply and Prevent
- Prevent configuration drift with automated policies
- Trigger alerts or roll-back of unauthorized changes
- Track improvements over time – prove your collaboration is secure!
With Avepoint PI, governance translates into:

- Automate & assure Never let out of control access controls get you twisted. Out of policy permissions, sharing settings, and membership restrictions are fixed automatically.
- Bulk up Create and manage Microsoft 365 Teams, SharePoint, Groups and OneDrive permissions, and security settings with batch controls to make initial configuration and updates easy.
- Security trimmed Security-trimmed access to one or multiple tenants means you can securely delegate insights and administration.
- Actionable reports Search for objects, users, permissions, or even actions with comprehensive reporting. Then, take swift, decisive action on the results.

- Audit & investigate Permissions nightmare? Shadow users? External users? Easily investigate users, items, deletions, and permissions changes with built-in reports.
- Who, what, & when Find out who’s got access to what content and then bulk edit to modify, remove, or copy settings for extra protection.
- Lockdown sharing Restrict access to and sharing of critical Microsoft 365 services, including Teams, SharePoint Online, Groups, OneDrive for Business, and their sites.
- Prioritize for how your clients work Permissions reports aren’t enough. Prioritize security insights based on how your clients define risk—whether government, industry, or organizational regulations and controls.

- Your own security service store Secure membership, security, and permissions across Teams, Groups, Sites, and OneDrive. Don’t settle for all-or-nothing tenant-wide controls. Implement security controls based on workspace context.
- Proof of work Respond to audit requests with reports on services, users, and configurations—including administrative actions—to easily validate service fees.
- Set it, forget it Once you enable security services, configuration drift can be reverted automatically. Or, notify users and admins of out-of-policy changes.